Wireless 802.11 System : Deauthentication Vulnerability
This post was originally published on my WordPress blog in 2017. I have decided not to rewrite it to preserve its original character during the migration. Enjoy the nostalgia (and the cringe)!
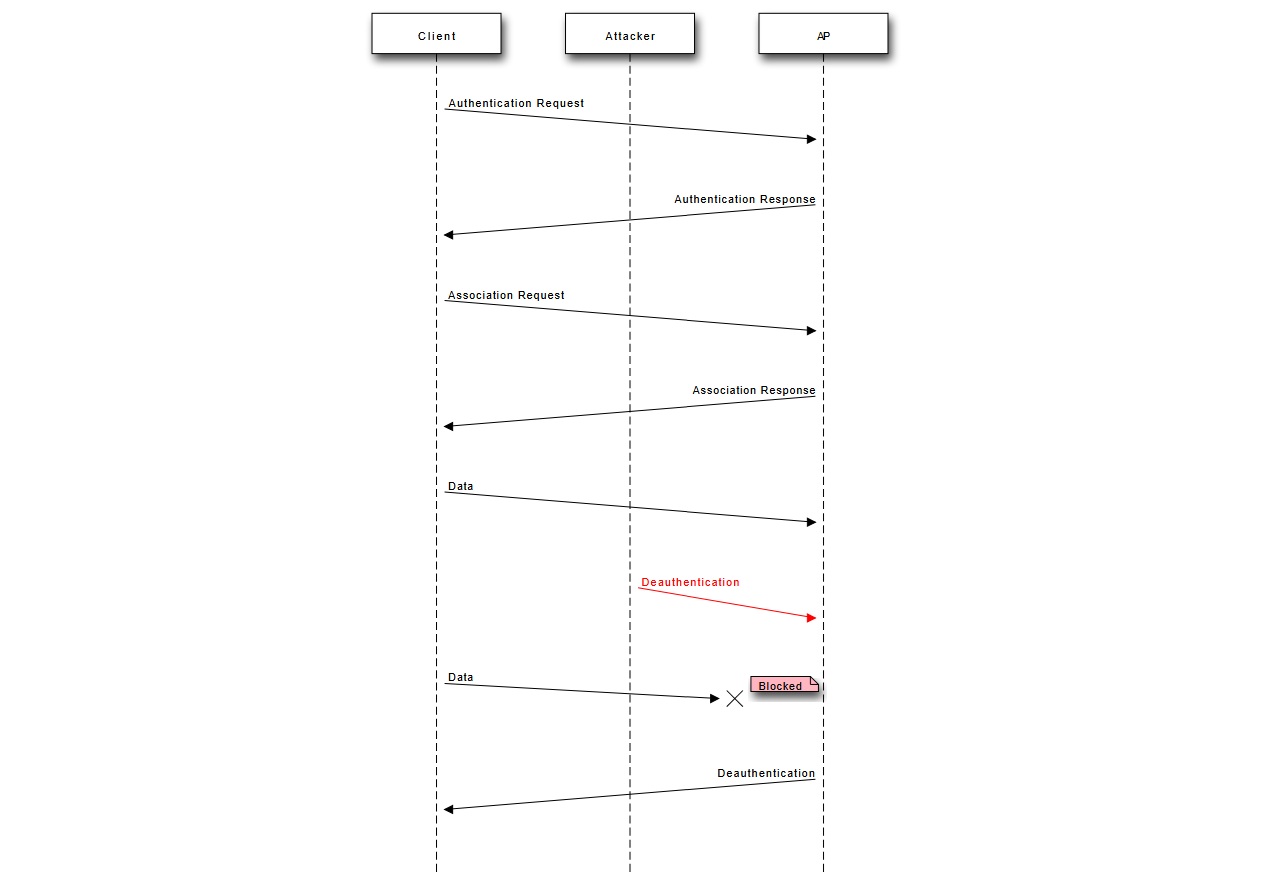
The IEEE 802.11 (WLAN) protocol contains the provision for a de-authentication frame. Sending the frame from the access point to a station is called a "sanctioned technique to inform a rogue station that they have been disconnected from the network".
(Image Source : Wikipedia)
But, an attacker can send a wireless access point a de-authentication frame at any time, with a spoofed address for the victim. The protocol does not require any encryption for this frame (before the 802.11w-2009 update), even when the session was established with Wired Equivalent Privacy (WEP) for data privacy, and the attacker only needs to know the victim's MAC address, which is available in the clear through wireless network sniffing.
Recently after testing this vulnerability with my router using a Kali-Linux installed PC and an RTL8192CU Adapter (WNA1000mV2) I wanted to perform the same without any computer and found this powerful library by Stefan Kremser for the ESP8266 Nodemcu version. I didn't lose a second for it and bought it, then flashed it and tested it. Though it was very funny, interesting and adrenaline making, I feared that even normal people could abuse the system by easily using this flaw. (As, you need only some $5 and watching a 2 minutes of YouTube video)
Though the 802.11 System got an update (802.11w-2009 update) for encrypting management frames :
from Wikipedia :
Protected frames :
Protection-capable management frames are those sent after key establishment that can be protected using the existing protection key hierarchy in 802.11 and its amendments.
Only TKIP/AES frames are protected and WEP/open frames are not protected
- Disassociation and de-authentication
- Radio measurement action for infrastructure BSS (802.11k frames)
- QoS action frame (802.11e frames)
- Future 11v management frames (802.11v frames)
Protection-capable Management Frames are protected by the same cipher suite as an ordinary data MPDU.
- MPDU payload is TKIP or CCMP encrypted.
- MPDU payload and header are TKIP or CCMP integrity protected.
- The protected frame subfield of frame control field is set.
- Only cipher suites already implemented required.
- Sender's pairwise temporal key (PTK) protects the unicast management frame, and the group temporal key (GTK) is used to protect the broadcast/multicast management frame.
- An RSN (802.11i) IE capability bit used to signal whether Protection-capable Management frames are protected.
BUT, from Stephan himself :
I tested it with different Wi-Fi networks and devices, it worked every time! It seems that even newer devices that support frame protection don’t use it by default.
While I don't condone the misuse of these vulnerabilities, they remain a persistent reality in our digital landscape. To help counter these threats, Stefan also developed a DeauthDetector library to identify active de-authentication attacks.